Hey, I’ve been working on a new IoT project and trying to decide between UDP and TCP for data transmission. Do you have any thoughts on why I might choose UDP for IoT applications?
Great question. UDP (User Datagram Protocol) can be an excellent choice for many IoT applications. It's lightweight, fast, and has lower overhead compared to TCP. This makes it ideal for devices that need to send small amounts of data quickly or have limited resources. What kind of data are you transmitting in your project?
I'm working on a smart agriculture system that transmits sensor data like temperature, humidity, and soil moisture from multiple field devices to a central server. The data isn't particularly sensitive, but needs to be sent frequently and in real time.
That's a perfect UDP application! In your scenario, it's more important to get the most recent data quickly rather than ensuring every single UDP packet arrives. UDP’s ‘fire-and-forget’ nature allows it to keep sending the latest readings without needing acknowledgments. This can significantly reduce latency and bandwidth usage, which is crucial for IoT devices with limited power and network resources.
That makes sense, but I'm a bit concerned about data loss. Won't using UDP mean some of our sensor readings might not make it to the server?
You're right to consider that. While some packet loss can occur with UDP, in many IoT applications, for your agriculture system, if you're sending frequent updates, losing an occasional reading won't impact the overall trend. Plus, you can implement a lightweight acknowledgment system at the application level if needed. The benefits of UDP's speed and efficiency often outweigh the potential for some data loss in IoT scenarios.
What is the UDP Protocol?
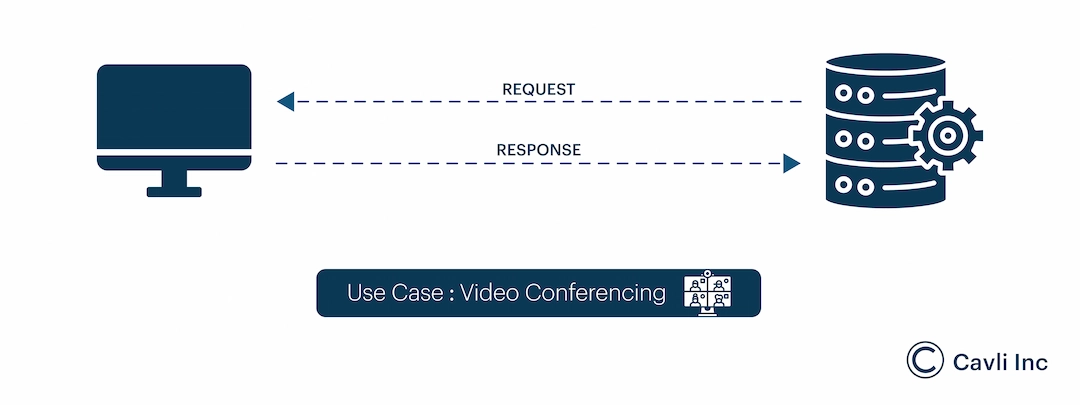
User Datagram Protocol (UDP) is a fundamental component of the internet protocol suite, playing a crucial role in facilitating fast and efficient data transmission across networks. As a lightweight, connectionless protocol, UDP offers a streamlined approach to sending data packets, making it an indispensable tool for applications that prioritize speed over reliability.
Basic UDP Protocol Functioning
Unlike its more famous cousin, Transmission Control Protocol (TCP), which ensures data integrity through rigorous error-checking mechanisms, UDP takes a different approach by sacrificing secure message delivery for reduced latency and overhead.
In the vast landscape of network protocols, UDP stands out as a versatile solution where real-time communication is paramount. Its simplicity and efficiency make it the popular protocol choice for applications such as online gaming, live streaming, and Voice over IP (VoIP) services.
For example, imagine you’re playing a multiplayer game where even minimal lag can affect gameplay. Its ability to transmit data quickly without the need for handshaking or acknowledgment, as in the TCP protocol, allows for seamless, low-latency experiences. Similarly, video streaming platforms leverage UDP to deliver content to viewers, ensuring a smooth and uninterrupted viewing experience.
The Architecture of UDP Protocol
The User Datagram Protocol (UDP) is a connectionless, lightweight transport layer protocol that allows applications to send data directly to the recipient without establishing a connection.
UDP Packet Format
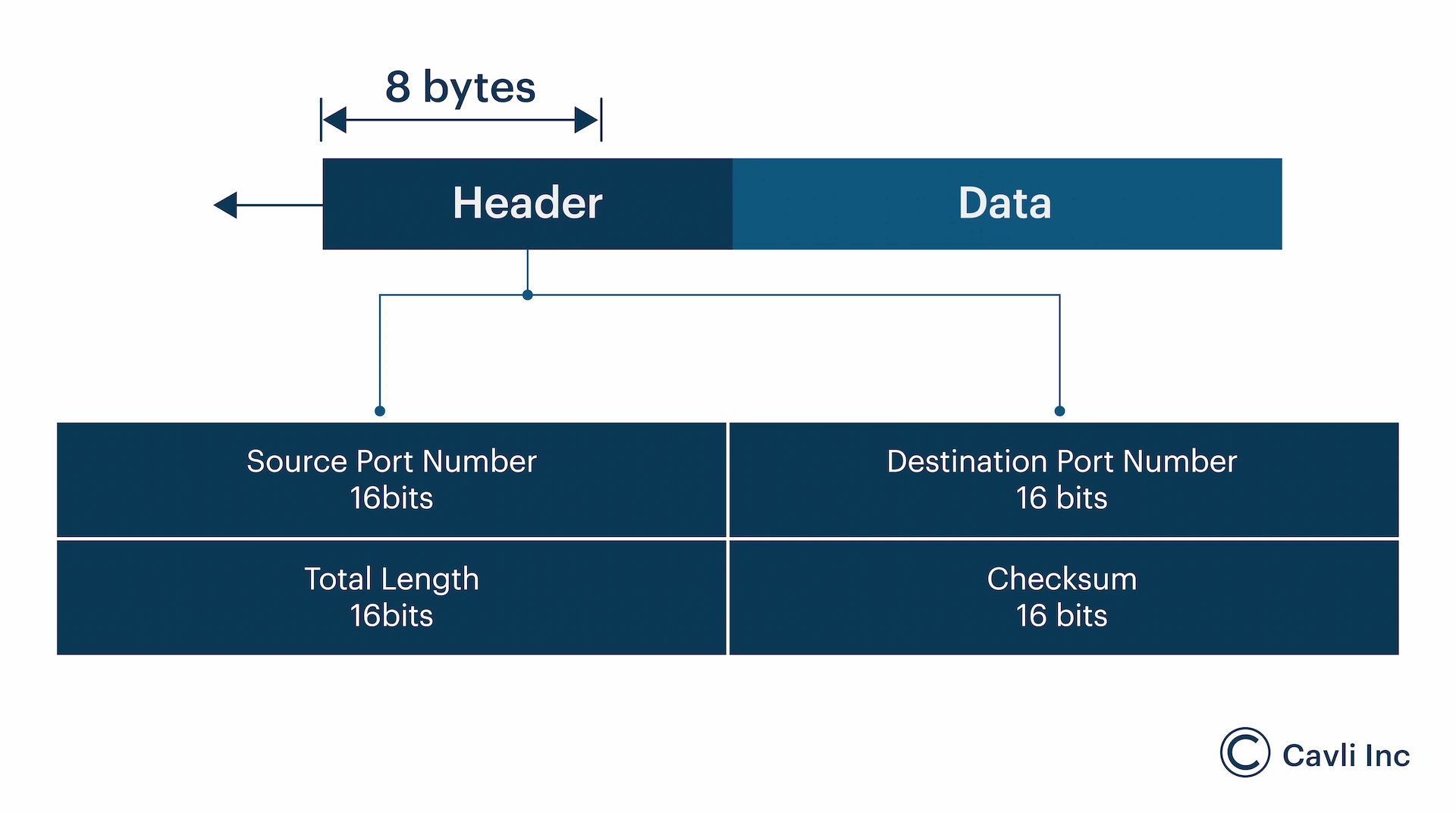
A UDP packet, also known as a datagram, consists of a header and a data section. The simplicity of the UDP packet format contributes to its efficiency. Here is the basic structure of a UDP packet:
- Header: 8 bytes long
- Data: Variable length, up to 65,535 bytes
UDP Header Structure
1. No Connection Establishment (Connectionless)
UDP operates in a connectionless mode, meaning it doesn’t require a handshake or connection setup before data transfer. Each packet, or datagram, is sent independently without maintaining a session state between sender and receiver. This makes UDP efficient for time-sensitive applications, as it minimizes overhead or the extra data and processing required to manage communication between systems, such as headers, error-checking, and control information, which can slow down transmission and reduce latency.
2. Datagram-Oriented Structure
UDP transmits data in discrete units called datagrams, which are independent packets containing both header and data sections. Each datagram is routed individually, potentially even taking different paths to the destination. It's often described as a "fire and forget" protocol – it sends the data and moves on, regardless of whether it reaches its destination.
3. UDP Header Structure
The UDP header is minimal, only 8 bytes long, which helps reduce processing time and bandwidth usage. It contains four main fields:
- Source Port (16 bits): Identifies the sending application's port number.
- Destination Port (16 bits): Identifies the receiving application's port number.
- Length (16 bits): Specifies the length of the entire datagram, including header and data.
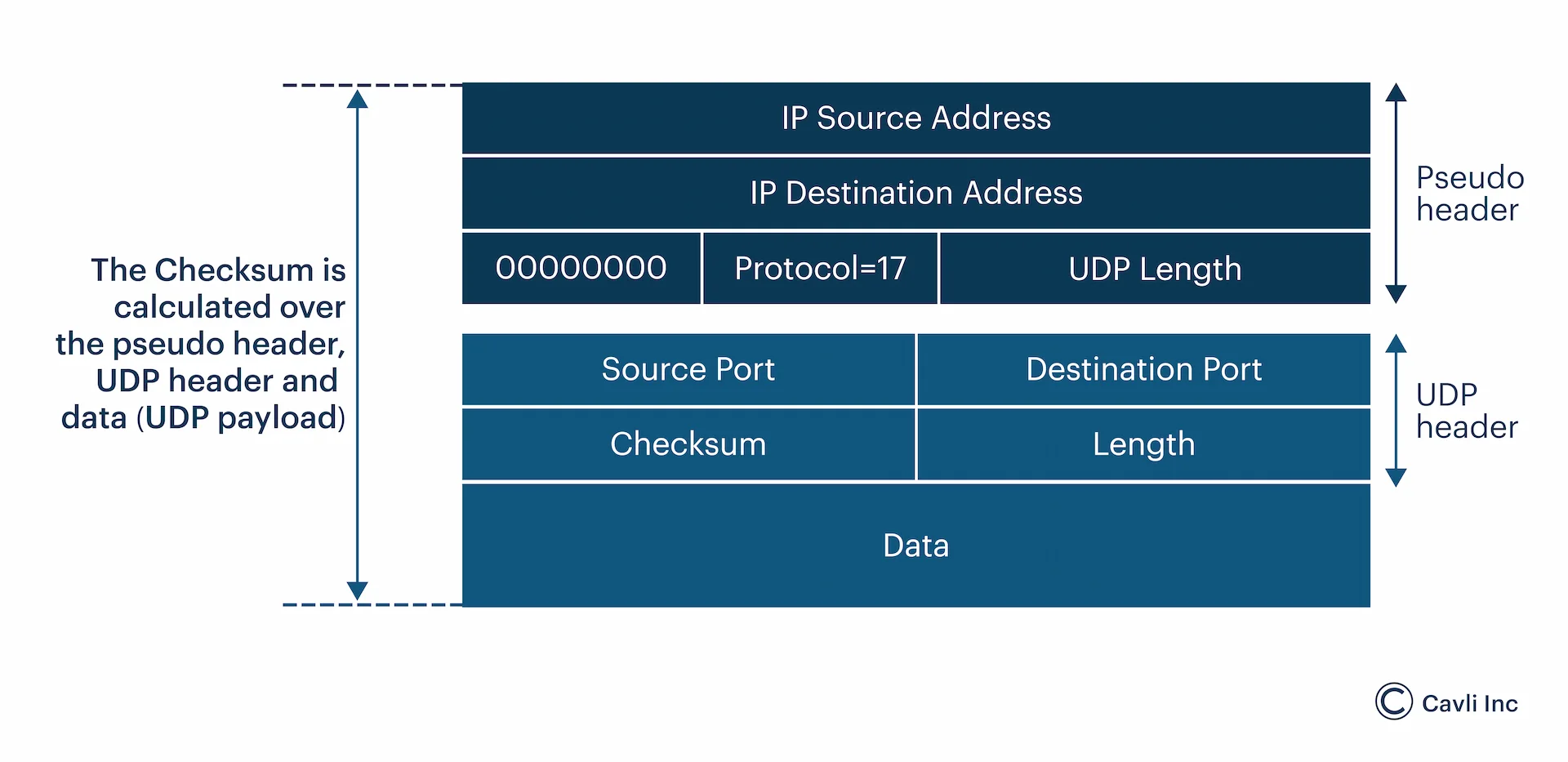
- Checksum (16 bits): Provides basic error-checking for the header and data; this is optional in IPv4 but mandatory in IPv6.
Checksum Error Checking
4. UDP Ports
UDP ports are identifiers for applications and services using the User Datagram Protocol. Since UDP is connectionless, these UDP port numbers allow communication without establishing a persistent connection. UDP ports are defined by numbers (0-65535) and are categorized as:
- Well-Known Ports (0-1023): Reserved for standard protocols like DNS (port 53), DHCP (ports 67/68), and NTP (port 123).
- Registered Ports (1024-49151): Assigned for specific services or applications.
- Dynamic/Private Ports (49152-65535): Used temporarily by applications for short-lived connections, often for internal communication.
UDP ports are essential for managing multiple services on a networked device without the overhead of connections.
5. Best-Effort Delivery
UDP uses a best-effort delivery mechanism, meaning there’s no guarantee that datagrams will reach their destination, arrive in order, or be free of errors. Unlike TCP, which resends lost packets, UDP simply transmits data as quickly as possible, trusting the application layer to handle any necessary retransmission or error correction.
6. Lack of Flow and Congestion Control
UDP doesn’t implement flow or congestion control mechanisms, as found in TCP. This simplicity allows for a fast transmission rate, but it also means that UDP can flood a network if not managed properly by the application. Applications using UDP, especially for high-throughput requirements like video streaming or gaming, must often implement their own methods for handling congestion.
In the ever-expanding universe of the Internet of Things (IoT), where billions of devices communicate vast amounts of data, choosing the right protocol is crucial. The User Datagram Protocol (UDP) has emerged as a key player in this space, offering a streamlined approach to data transmission that aligns perfectly with many IoT requirements.
How Does UDP Protocol Work?
To understand UDP's operation, let's break it down into simple steps:
Packaging the Data
The process begins when an application decides to send data using UDP. This could be anything from a DNS query to a chunk of streaming video data. It packages the data into a UDP datagram.
Adding Headers & Datagram Assembly
The UDP layer constructs a header containing the source and destination port numbers, the length of the datagram, and a checksum for basic error detection. The UDP header is prepended to the application data, forming a complete UDP datagram. The UDP datagram is then encapsulated into an IP packet.
IP Layer Handoff & Link Layer Encapsulation
The UDP datagram is passed to the Internet Protocol (IP) layer, which adds its own header containing source and destination IP addresses. The IP packet is then encapsulated in a link-layer frame (e.g., Ethernet) for transmission over the physical network.
Network Transmission & Recipient Processing
The frame is sent over the physical network, potentially traversing multiple routers and network segments. Upon reaching the destination, the process is reversed. The link layer frame is stripped, the IP layer processes its header, and the UDP datagram is extracted.
UDP Layer Processing & Reception
The destination device's UDP layer verifies the checksum (if used) and identifies the target application based on the destination port. Upon reaching the destination, the receiving device extracts the UDP datagram from the IP packet. The receiving application then extracts the data from the UDP datagram.
Advantages of User Datagram Protocol
- Minimal Overhead for Frequent, Small Data Transfers: UDP’s lightweight protocol structure makes it ideal for applications that frequently transmit small amounts of data. This is especially beneficial for IoT devices, which often need to send periodic sensor readings or status updates with minimal power consumption and efficient network utilization.
- Efficient Broadcast and Multicast Support: UDP supports broadcast and multicast transmissions, enabling the simultaneous distribution of data to multiple recipients. This capability is crucial for applications like online multiplayer games and distributed systems that need to keep multiple nodes synchronized with real-time updates.
- Streamlined and Rapid Packet Processing: With its simplified architecture, UDP allows for fast packet processing and minimal overhead. This is particularly valuable in IoT applications, where devices may have limited processing power and battery life, allowing for effective communication without taxing device resources.
- Optional Error Detection and Custom Reliability: UDP includes an optional error-checking mechanism, allowing applications to build custom protocols on top of UDP for cases where reliability is required. This is useful for specific applications, like file transfer or messaging systems, that need a balance of speed and delivery assurance.
- Optimized for Low-Power Devices: The minimal protocol requirements and lack of a connection setup allow devices to quickly “wake up” to transmit data and return to a low-power state, which is particularly advantageous for battery-powered IoT devices seeking to minimize power usage.
- Stateless Nature for High Scalability: UDP is a connectionless protocol and doesn’t maintain session states, making it highly scalable and suitable for applications requiring high volumes of simultaneous connections, such as DNS services, IoT networks, or streaming platforms.
- Reduced Impact from Network Congestion: Lacking built-in congestion control, UDP can transmit data continuously, even in congested networks. This characteristic makes it ideal for critical real-time data applications, such as telemetry or emergency alert systems, where delays or interruptions could impact service reliability.
TCP Protocol vs UDP Protocol
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are both transport layer protocols in the Internet Protocol suite but serve different purposes. The Transmission Control Protocol (TCP) is a core protocol in the Internet Protocol (IP) suite that ensures reliable, ordered, and error-checked delivery of data between devices over a network. TCP establishes a connection-oriented communication channel, meaning it sets up a virtual connection between sender and receiver before data transfer, using a three-way handshake. It manages flow control, error checking, and packet retransmission to guarantee data integrity, making it ideal for applications where accuracy is essential, such as web browsing, email, and file transfers.
| Parameter | Transmission Control Protocol (TCP) | User Datagram Protocol (UDP) |
|---|---|---|
| Type of Service | Connection-oriented; requires establishing and closing connections. | Datagram-oriented; no need for connection setup, maintenance, or termination. Efficient for broadcast/multicast. |
| Reliability | Reliable; ensures data delivery to the destination. | Unreliable; does not guarantee data delivery to the destination. |
| Error Checking Mechanism | Extensive; includes error-checking, flow control, and acknowledgments. | Basic error checking through checksums. |
| Acknowledgment | Acknowledgments ensure data is received, confirming packet delivery. | No acknowledgment segment; delivery is not confirmed. |
| Sequence | Packets are sequenced to arrive in order, managed by TCP. | No sequencing; packet order is not preserved and must be managed by the application layer if needed. |
| Speed | Slower due to error checking, acknowledgments, and sequencing. | Faster, simpler, and more efficient, with low overhead. |
| Retransmission | Retransmits lost packets to ensure complete delivery. | No retransmission of lost packets; dropped packets are simply discarded. |
| Header Length | Variable length, between 20-60 bytes, depending on options. | Fixed-length header of 8 bytes, making it more efficient. |
| Weight | Heavyweight due to connection management, sequencing, and error control. | Lightweight, with minimal management, leading to higher efficiency. |
| Handshaking Techniques | Uses a three-way handshake (SYN, SYN-ACK, ACK) to establish connections. | Connectionless; no handshake or initial connection setup. |
| Broadcasting | TCP lacks support for broadcasting. | UDP supports broadcasting and multicasting, useful for IoT and streaming. |
| Stream Type | Byte stream; data is managed as a continuous stream for precise sequencing. | Message stream; treats each datagram as a discrete, self-contained message. |
| Overhead | Higher overhead, though it provides reliability features. | Very low overhead, ideal for applications needing low latency. |
| Header Content | Source port, destination port, sequence number, acknowledgment number, data offset, reserved bits, control flags, window, checksum, urgent pointer, and options. | Source port, destination port, length, checksum. |
| Protocols Supported | Used by HTTP, HTTPS, FTP, SMTP, Telnet. | Used by DNS, DHCP, TFTP, SNMP, RIP, and VoIP. |
| Applications | Used where reliable, secure communication is needed, such as web browsing, email, file transfer, and military systems. | Used where speed is prioritized, and reliability is less critical, such as VoIP, video streaming, gaming, and IoT applications. |
UDP Applications In Action: Real-World Use Cases
Internet of Things
- UDP's connectionless nature allows IoT devices to transmit data quickly and then return to a low-power state, significantly extending battery life in remote or difficult-to-access sensors. It enables implementation on devices with limited processing power and memory, such as environmental sensors or smart home appliances, allowing for cost-effective and scalable IoT solutions.
- For example, in a smart agriculture system, soil moisture sensors might use UDP to send periodic readings to a central control unit. The sensors can wake up, transmit data, and return to sleep mode rapidly, conserving power while still providing timely information for irrigation management.
Live Media Streaming
UDP's low latency makes it an excellent choice for streaming audio and video content:
- Live streaming platforms often utilize UDP for real-time video delivery, accepting occasional artifacts or frame drops in exchange for minimal delay between the source and viewers.
- Consider a live sports broadcast: UDP allows for near-real-time transmission of video and audio, ensuring viewers experience the action with minimal delay. Even if some packets are lost, resulting in brief quality dips, the overall viewing experience remains smooth and timely.
- Voice over IP (VoIP) services rely heavily on UDP to transmit audio packets, prioritizing immediate delivery over perfect fidelity to maintain natural conversation flow.
UDP is preferred for time-sensitive applications like VoIP and streaming. Although UDP lacks reliability, minor data loss is manageable in these applications, which prioritize reduced latency over perfect data integrity.
To learn more about VoIP and its modern services, navigate to our blog VoLTE In IoT.
DNS and DHCP
Fundamental internet protocols like DNS (Domain Name System) and DHCP (Dynamic Host Configuration Protocol) rely on UDP for their core functions:
- DNS queries typically use UDP for initial lookups due to its speed and efficiency in handling small, frequent requests, falling back to TCP only for larger responses or when reliability is crucial.
- DHCP leverages UDP's ability to broadcast messages, allowing devices to quickly obtain network configuration information without the overhead of establishing individual connections.
- For instance, when you type a web address into your browser, your device sends a UDP-based DNS query, which retrieves the IP address associated with a domain name. This process occurs so quickly that users rarely notice the underlying lookup mechanism.
DTLS (Datagram Transport Layer Security)
With DTLS, UDP adapts the security features of TLS (used with TCP), providing encryption and authentication for datagram-based applications:
- DTLS enables secure communication for UDP-based protocols, crucial for applications like WebRTC that require protected peer-to-peer data exchange.
- It maintains UDP's connectionless nature while adding a handshake mechanism for establishing secure sessions, balancing security with performance.
- For example, a secure IoT ecosystem might employ DTLS to encrypt sensor data transmitted over UDP, protecting sensitive information from eavesdropping or tampering without significantly impacting communication efficiency.
HTTP/3 and QUIC Protocols
HTTP/3, the latest version of the Hypertext Transfer Protocol, and QUIC (Quick UDP Internet Connections) represent significant advancements in web technology, both built on UDP:
- QUIC, developed by Google, uses UDP as its transport layer to provide faster connection establishment and improved performance in high-latency or lossy network environments.
- HTTP/3 leverages QUIC to offer reduced latency, improved multiplexing, and better handling of network changes, enhancing the overall web browsing experience, especially on mobile devices or unreliable networks.
- For example, a content delivery network (CDN) implementing HTTP/3 can significantly reduce page load times for users accessing websites from various global locations. The protocol's ability to handle multiple streams independently over a single connection allows for more efficient resource loading, beneficial for complex web applications with numerous assets.
Cavli Wireless IoT Connectivity Modules
Closing Notes
The User Datagram Protocol (UDP) remains essential in modern networking for applications where speed, efficiency, and low latency are paramount. Its streamlined structure and connectionless design enable rapid data transmission, making it ideal for real-time services like streaming, gaming, and IoT. However, UDP's lack of built-in reliability requires developers to implement tailored solutions to manage data integrity and packet loss in critical applications. As networking evolves—especially with advancements in IoT and 5G —understanding and leveraging UDP's strengths and limitations will allow engineers to optimize performance, reduce overhead, and maintain high-speed connections even in complex, large-scale networks. By combining UDP’s core efficiency with enhanced error handling or security measures where needed, it’s possible to create versatile, high-performance networks suited for the demands of today’s fast-paced digital ecosystem.
Amusing Tech Chronicles
Facts and Anecdotes Related to this Edition of Wireless By Design
The Newspaper Delivery
UDP IP protocol is like a newspaper delivery service that tosses papers onto driveways as fast as possible. They don’t check if each paper lands perfectly at the door—if one’s missed, they’re already on to the next house. This represents UDP’s "best-effort" delivery, suitable for applications like DNS queries where speed matters more than perfect delivery.
The Postal Service of the Internet
The Postal Service of the Internet Imagine UDP IP protocol as the postal service of the internet, but with a twist. It's like a super-efficient mail carrier who's always in a hurry. They'll take your letter (data packet) and zoom off to deliver it as fast as possible. Sometimes, they might drop a letter or give it out of order, but they're so quick that you can just send another one right away!
The Open-Air Announcer
Imagine a UDP IP protocol-based communication as a group of people shouting messages across a field. Each person sends their message out loud, without waiting for a reply or ensuring that everyone heard it perfectly. Some might miss the message, but the exchange is fast and allows constant interaction, ideal for scenarios like VoIP where minimal delay is critical.
Go Beyond and Explore
UDP IP protocol is often used for VPNs (Virtual Private Networks) because of its speed and efficiency. VPNs need to handle a lot of small, time-sensitive packets, and UDP's low overhead and quick transmission make it ideal for this purpose. Additionally, UDP's stateless nature allows VPN connections to be more resilient to network changes, which is particularly useful for mobile users. While UDP doesn't guarantee packet delivery, VPN software can implement its own reliability mechanisms when necessary, maintaining the benefits of UDP's speed while ensuring data integrity.
The UDP protocol itself is not inherently secure. It does not provide built-in encryption or authentication mechanisms. However, this doesn't mean that UDP-based communications can't be secure. Security in UDP-based applications is typically implemented at the application layer or by using additional protocols. For example:
- DTLS (Datagram Transport Layer Security): DTLS can be used to encrypt UDP network communications, providing confidentiality and integrity.
- VPNs: VPNs often use UDP as a transport protocol but implement their own encryption and authentication mechanisms.
- Application-Specific Security: Applications can incorporate encryption, authentication, and integrity checks directly in the application layer for additional security.
In IoT contexts, it's crucial to implement appropriate security measures when using UDP, especially for sensitive data or control commands.
Diagnosing UDP IP protocol issues requires specialized tools:
- Wireshark: Captures and inspects UDP packets to identify packet loss or malformed datagrams.
- iperf3: Measures network performance by generating UDP traffic to analyze throughput and packet loss.
- netstat and ss: Monitors network connections and UDP port numbers to locate potential conflicts.
Example: For VoIP troubleshooting, use Wireshark to capture packets and analyze patterns of packet loss or jitter affecting call quality.
Since UDP is connectionless, it can face challenges with firewalls and NAT (Network Address Translation), especially in peer-to-peer or real-time communication scenarios. Here are some key practices for navigating these obstacles:
- STUN/TURN Protocols: The STUN protocol helps UDP-based applications discover the public IP and port information they need to establish connections through NAT. TURN is used as a fallback in strict NAT or double-NAT environments, relaying traffic for peer-to-peer applications like WebRTC.
- UDP Hole Punching: This technique allows two devices behind NAT to establish a direct UDP connection, useful in online gaming and peer-to-peer applications where low latency is essential.
- Firewall Configuration: To ensure secure and reliable UDP traffic, configure firewalls to allow specific UDP ports while balancing security needs. Limiting access to necessary applications helps prevent unauthorized traffic.
Example: WebRTC, used in video conferencing, employs both STUN and TURN servers to facilitate seamless peer-to-peer connections, even when participants are behind NAT or firewall restrictions.


Leave a comment
Note: if you need support, please contact our support team and do not use the comment form. Your email address will not be published.