Machine-to-Machine (M2M) communication is a key part of the Internet of Things (IoT), enabling devices to communicate autonomously. M2M in IoT connects these devices, allowing them to share data and perform actions without human intervention. As we enter the Fourth Industrial Revolution, understanding how M2M communication fits into the broader IoT architecture is essential for harnessing the power of automation.
M2M Communication in IoT
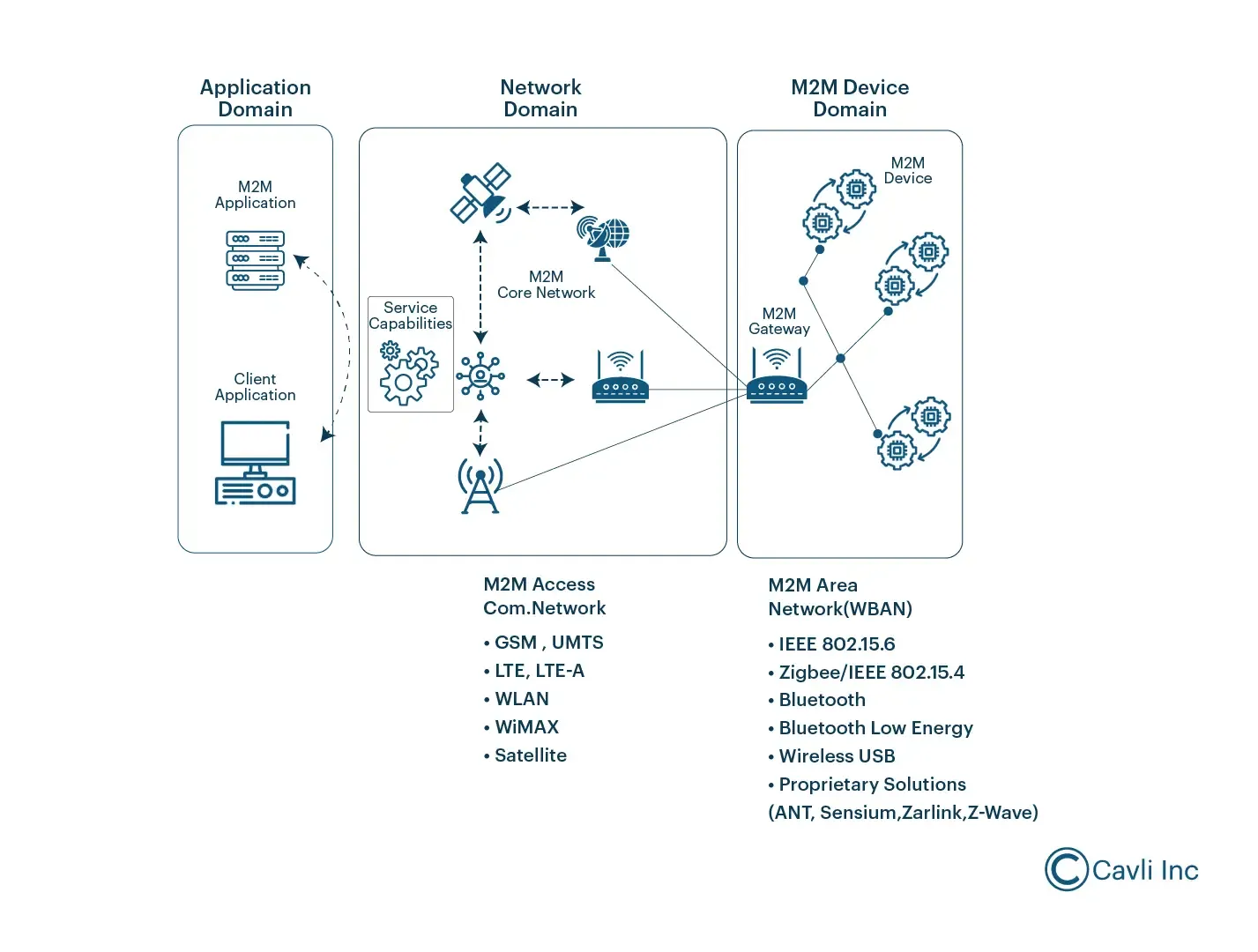
M2M communication system
In M2M in IoT, devices communicate directly with each other without needing internet connectivity, allowing for autonomous actions. This M2M architecture in IoT involves various components like sensors, communication networks, and processors to ensure seamless connectivity. These systems use both wired and wireless communication channels to transfer data and execute tasks autonomously.
M2M Communication typically involves a sensor that measures data,RFID, network infrastructure for enabling data transmission over communication channels, and another machine/network entity that interacts or performs actions without human interference. It allows point-to-point contact across these components of M2M connectivity.
How M2M in IoT Enables Connectivity
M2M communication evolved alongside advancements in wireless technologies, particularly in the late 1990s and early 2000s. This evolution made M2M in IoT an essential component, enabling autonomous data exchange and paving the way for IoT applications that span industries. This evolution set the stage for the large-scale implementation of IoT systems, connecting a variety of devices seamlessly.
In today's connected world, M2M and IoT applications are revolutionizing the way we interact with our environment. M2M solutions enable devices to communicate directly.
In this blog, let's unravel the insights into the evolution of M2M technology and its role in shaping the future of connectivity, covering the fundamental concepts, architecture, and practical applications of Machine to machine connectivity.
The Evolution of M2M Communication
Machine-to-Machine (M2M) communication, initially popularized with systems like Caller ID, has evolved significantly. M2M in IoT has now become integral to various IoT applications, contributing to the seamless operation of connected devices across industries. But the real game-changer came with the rise of Cellular M2M Communication.
"Siemens launched the GSM data module M1, for industrial M2M applications, enabling wireless communication between machines using GSM technology."
This paved the way for today’s mighty Wireless Modules. In the 21st century, these modules have incorporated cutting-edge features such as Global Positioning Systems (GPS), Machine to Machine Identification Modules (MIMs), and embedded Java, enabling support for Internet of Things (IoT) applications. It also now incorporates lightweight publish/subscribe reliable messaging protocol for machine to machine/ IoT devices.
Understanding M2M Technology: The Harmonious Machine-to-Machine Communication in Connected Networks
M2M in IoT technology automates the exchange of data between devices, enabling real-time monitoring and autonomous actions. This exchange is a critical function in the broader IoT architecture, facilitating smarter connected environments.
Imagine a large manufacturing facility filled with various types of machinery.
In this Machine to machine connectivity system, sensors are installed on each piece of equipment. These sensors continuously collect data on a machine's performance, such as temperature, speed, or vibration levels, acting as the eyes and ears of the facility.
When these sensors detect anything out of the ordinary—a temperature high, or an irregular vibration—they automatically send this data to a central management system. This is done through an M2M network that allows machines to talk to each other and to the system, without human assistance.
The management system then analyzes this data in real-time and predicts if any potential failure is to happen soon to trigger a maintenance request. This predictive maintenance approach in the M2M system is crucial because it allows the facility to address problems before they lead to machine breakdowns, minimizing downtime and maintaining productivity.
Key Components in M2M Communication and IoT Architecture
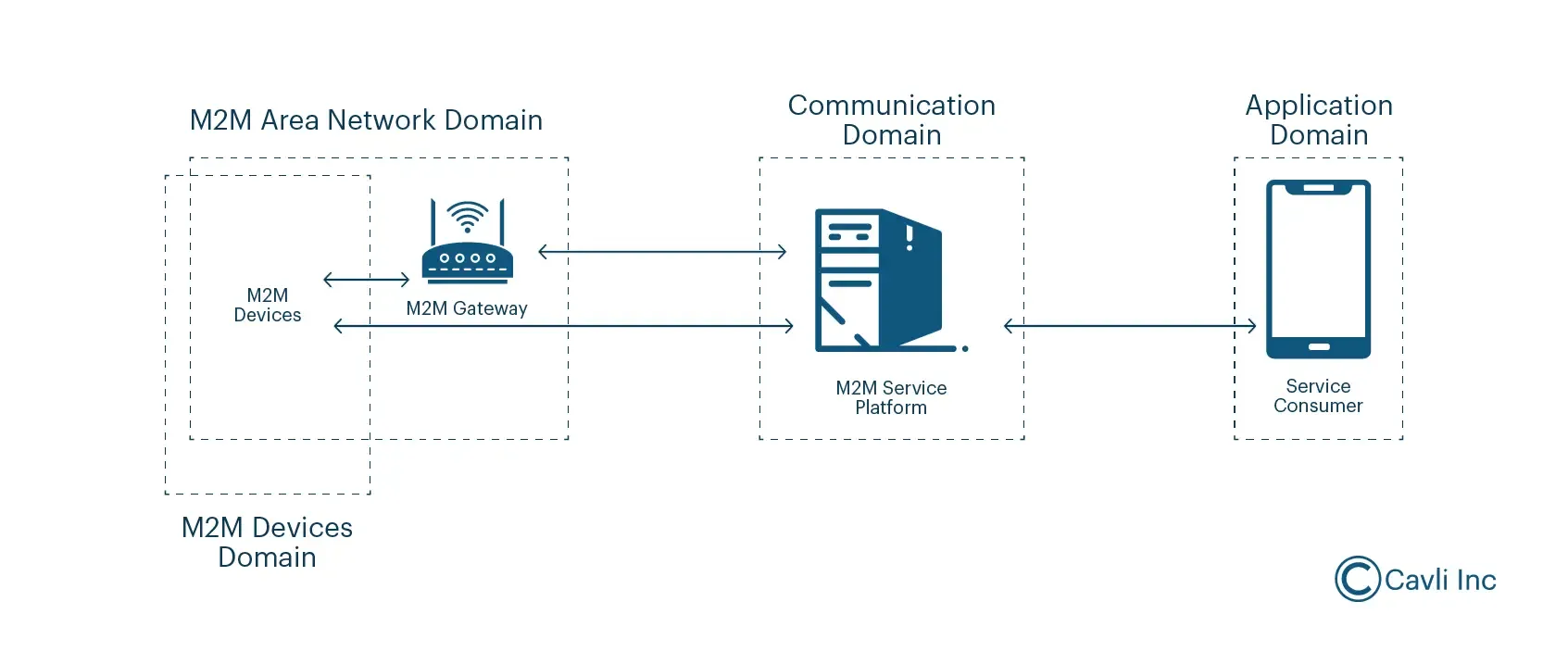
Working of an M2M system is depicted here.
The key components driving M2M in IoT systems include:
Sensors
Sensors are compact devices designed to detect and measure physical properties or changes in the physical environment/M2M networks, and convert these into electrical/optical signals that can be measured and analyzed, forming the foundation for subsequent processing and decision-making.
To know more about sensors, read our blog on Sensors in IoT .
Communication Networks
M2M systems rely on various networks, including cellular, Wi-Fi, Bluetooth, and satellite connections, to transmit data between M2M devices and central systems. The choice of network depends on factors like range, bandwidth, and power consumption.
Data Processing Units
Once transmitted, the collected data from machine to machine networks is processed by embedded systems, computers, or cloud-based servers, to analyze and interpret the information using predefined algorithms, and generate actionable insights.
Software Applications
These applications manage the entire M2M system, providing interfaces for configuring M2M devices, setting communication protocols, visualizing data, and triggering automated responses. By automating routine tasks and enabling real-time data monitoring, M2M technology enhances operational efficiency, reduces costs, and improves decision-making processes across various industries.
Types of M2M Communications and Network Topologies in Device Networking
Wired M2M
Wired M2M (Machine to Machine) communication uses physical cables to connect devices, ensuring stable, reliable, and secure data exchange. Wired M2M connectivity supports high data transfer rates and low latency, making it ideal for high-bandwidth and real-time applications.
Wired M2M is well-suited for industrial automation, building management systems, and utility metering. Although it involves higher initial installation costs due to cabling, its long-term reliability and lower maintenance needs can be advantageous. Wired M2M is also less flexible regarding device mobility.
Wireless M2M
Wireless M2M (Machine to Machine) communication enables devices to exchange data without physical connections, using wireless technologies.
Wi-Fi Networks
Wi-Fi networks offer reliable data transmission suitable for M2M applications within confined areas like factories, warehouses, and office buildings, enabling devices to connect to local area networks (LANs) for efficient communication. This connection is known as M2M LAN or Machine to Machine Local Area Network.
Cellular Networks
Cellular networks offer widespread coverage in M2M communication. Cellular networks can support a large number of devices, making them suitable for large-scale M2M applications and enabling data transmission over longer distances.
Satellite Networks
Satellite networks are crucial for M2M applications in remote or hard-to-reach locations where cellular and Wi-Fi coverage is unavailable, allowing devices to communicate globally. Wireless M2M connectivity is ideal for maritime, aviation, and remote environmental monitoring applications.
To learn more about these cellular and satellite networks, read our blog A Guide on Cellular IoT and Satellite IoT .
Wireless M2M connectivity is ideal for applications requiring frequent data updates and mobility, such as smart metering or connected vehicles. It offers flexibility and mobility, allowing devices to operate in diverse and remote locations without the constraints of wired infrastructure.
While Wireless M2M connectivity provides ease of deployment and scalability, it can be less reliable than wired M2M systems due to signal interference and coverage issues. Security and data integrity are also key considerations in wireless M2M connectivity.
Key Features of M2M Connectivity
Swift Event Detection
Swift event detection in M2M systems refers to the rapid identification and response to significant occurrences, errors, or changes in the interconnected devices within the M2M network. This capability is essential for maintaining optimal performance, safety, and efficiency in various M2M applications.
Flexible Data Transmission
M2M Communication incorporates features like time control and time tolerance in M2M systems, enabling a smooth data transfer between devices. While time control refers to the ability to precisely control and manage the timing of events in a machine to machine system. Time tolerance refers to the acceptable deviation from the expected timing of events in a machine to machine (M2M) system.
Remote Monitoring
Remote monitoring in M2M networks allows for managing and monitoring crucial M2M devices from a central M2M platform. This helps to track real-time updates and control devices from anywhere in the world. This is an indispensable feature for applications like healthcare, industrial manufacturing, etc.
Scalability
Scalability of M2M networks plays an important role as the connected devices are growing day by day. M2M Technology should be future-proofed to handle increasing numbers of connected devices. It should also support onboarding and provisioning of devices and the large volumes of data generated by M2M devices.
Automation
Automation in M2M networks plays a significant role in boosting efficiency by enabling real-time monitoring and control, reducing human intervention. It enhances accuracy and consistency, minimizing errors and operational costs. M2M networks support predictive maintenance, by identifying issues early and preventing downtime.
How M2M Communication Drives Seamless Device Interaction in the IoT Ecosystem
M2M Communication is the key to direct device-to-device interaction in the Internet of Things (IoT). Unlike the broad IoT network, where multiple devices connect over the internet, M2M enables machines to communicate autonomously without human intervention. This foundational communication allows devices to share data and make decisions on their own.
In M2M in IoT, devices use lightweight protocols like MQTT to exchange small amounts of data efficiently, even in low-bandwidth environments. Embedded Java ensures smooth integration across various devices, allowing them to work together seamlessly, regardless of the manufacturer or operating system.
From smart homes to industrial automation, M2M communication makes these systems work smarter by enabling real-time updates and automating processes. Whether in healthcare or manufacturing, M2M ensures devices collaborate to optimize performance and efficiency, making IoT a powerful tool for innovation.
To learn more about the role of lightweight protocol in IoT, read our blog on Message Queuing Telemetry Transport/MQTT protocol .
Differences Between IoT and M2M: IoT vs M2M
| Feature | IoT (Internet of Things) | M2M (Machine to Machine) |
|---|---|---|
| Connectivity | Uses internet protocols (HTTP, FTP, Telnet). | Direct point-to-point connections (cellular, wired). |
| Communication Type | Supports diverse communication methods. | Relies on traditional communication technologies. |
| Internet Dependency | Requires internet connectivity for operation. | Can function without internet. |
| Cloud Integration | Frequently integrates with cloud services. | May not always rely on cloud computing. |
| Data Handling | Processes large volumes of data for advanced analytics. | Transfers small, specific datasets with limited analysis. |
| Intelligence | Devices have embedded intelligence for decision-making. | Limited intelligence; primarily relies on predefined instructions. |
| Scalability | Highly scalable, supporting numerous devices. | Scalability is more limited due to direct connections. |
| API Integration | Supports open API integrations for system extensibility. | Does not support open API integration. |
| Scope of Use | Covers a wide range of applications (smart cities, health, etc.). | Typically used for specific machine-related applications. |
| Device Requirements | Can use generic, commodity devices. | Requires specialized device solutions. |
| Data Sharing | Facilitates data sharing across multiple applications. | Data sharing is restricted to communicating devices only. |
| Business Model | Supports B2B and B2C models. | Primarily B2B (Business to Business). |
| Communication Protocols | Uses internet-based protocols (e.g., MQTT, HTTP). | Often uses traditional communication protocols (e.g., GSM). |
| Role in Automation | Plays a key role in the automation of entire ecosystems. | Focuses on direct machine-to-machine communication. |
| Example Use Cases | Smart homes, health monitoring, environmental sensing. | Fleet management, industrial machine monitoring. |
The difference between IoT and M2M lies in the scope, scale, and purpose of their communication. While both technologies are integral to the world of connected devices, they differ in how they enable devices to communicate and the complexity of their operations.
M2M communication refers to the direct exchange of data between devices without human intervention. It is typically used in specific, localized contexts where a small number of devices communicate for predefined tasks, such as in industrial machinery or fleet management systems. M2M communication primarily focuses on point-to-point communication between devices, ensuring that data flows securely and efficiently within a limited network.
In contrast, IoT (Internet of Things) involves a much broader ecosystem. IoT connects devices to the internet and to each other, creating a network where devices can share data across vast distances and interact through cloud platforms. IoT systems integrate multiple M2M communication connections into an interconnected network that enables more complex applications, from smart cities to healthcare systems.
While M2M communication is often a subset of IoT, IoT takes things a step further by allowing devices to communicate not only with each other but also with centralized systems and data platforms, making the entire network smarter and more adaptable. Understanding the difference between IoT and M2M is crucial for businesses looking to integrate either M2M communication or IoT technology into their operations, as each serves different purposes based on the level of interaction and the scale of the network. The difference between IoT and M2M becomes even clearer when considering the complexity of their applications and how they impact industries like healthcare, manufacturing, and smart cities.
M2M Architecture in IoT
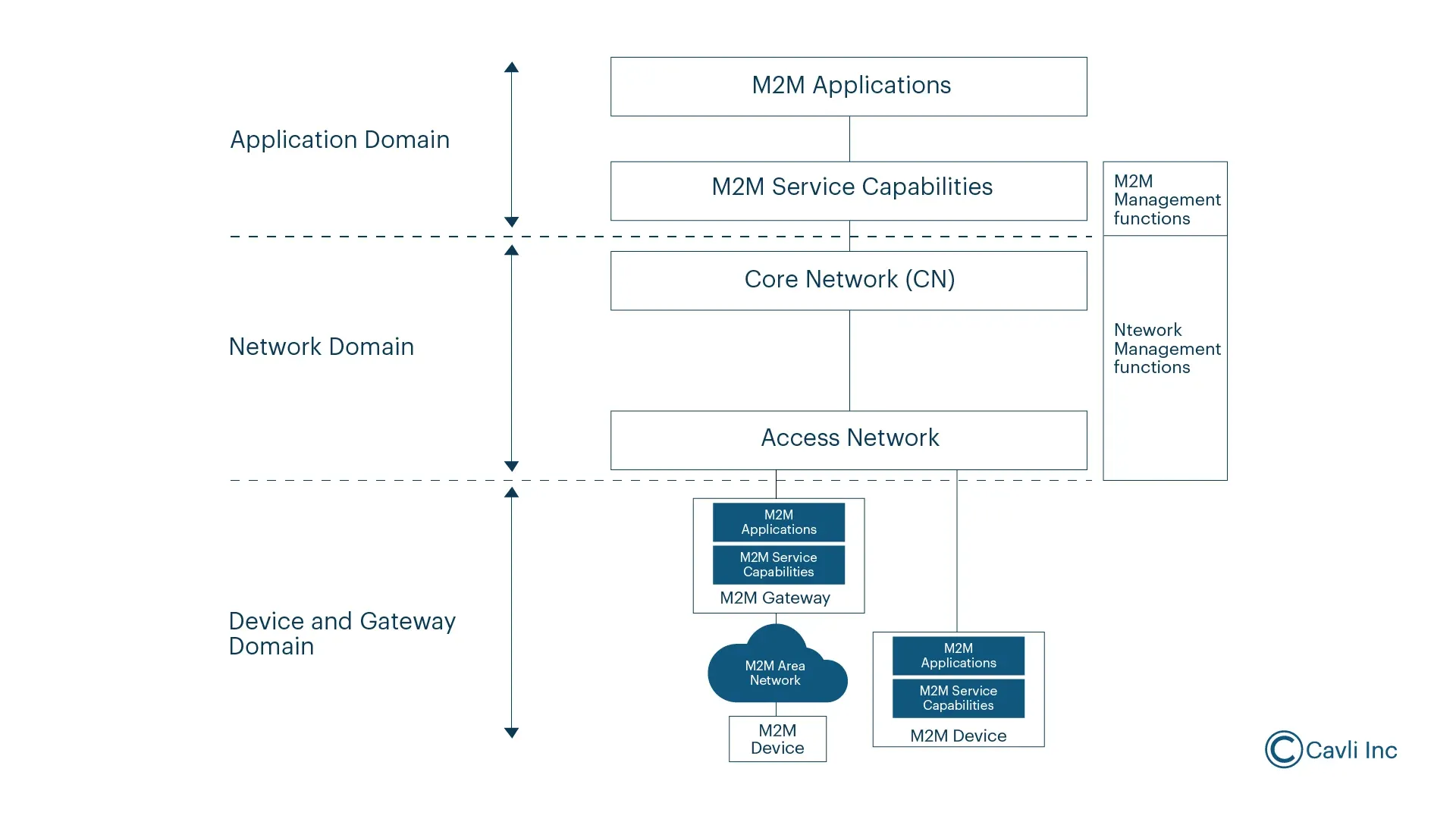
Detailed M2M architecture is depicted here.
The M2M architecture in IoT systems comprises several core elements that ensure seamless communication and data processing:
Device Layer
The device layer includes the physical devices that collect data (sensors) and perform actions (actuators) based on received commands. These M2M devices are often embedded with communication modules that allow them to connect to various networks and other devices. It serves as the entry point for data into the M2M system, facilitating M2M communication across IoT networks. This layer forms the foundation for M2M in IoT, enabling devices to share real-time data, which is crucial for intelligent automation.
A key component of this layer is sensor integration. The devices use sensors to measure environmental or operational conditions, making it a critical element in M2M communication in IoT, where real-time data is vital for decision-making processes.
Communication Layer
The communication layer in M2M architecture consists of gateways that serve as intermediaries between devices and the network. These gateways aggregate and convert data into a format suitable for transmission across various communication channels. The M2M communication in IoT relies on several protocols, such as Wi-Fi, cellular, Bluetooth, Zigbee, and LPWAN (Low Power Wide Area Networks). Each of these technologies plays a crucial role in the overall M2M architecture in IoT by ensuring that devices can connect and exchange data over the most suitable network.
The rise of 5G networks has further enhanced the capabilities of this layer, allowing for real-time communication and supporting critical IoT applications such as autonomous vehicles, healthcare, and industrial automation, where low latency and high bandwidth are required.
Application Layer
The application layer is where IoT applications and services reside. It enables M2M communication in IoT by interacting with the services layer to manage data and control devices. This layer ensures that the collected data can be shared with other systems for advanced analytics and decision-making. By facilitating real-time data exchange, it plays a key role in the success of M2M in IoT deployments across industries like smart homes, healthcare, and manufacturing.
Examples of applications in this layer include smart energy management systems, predictive maintenance in industrial IoT, and healthcare IoT applications, all of which rely on seamless M2M communication to function effectively.
Common Services Layer
The services layer acts as a bridge between IoT devices and communication networks. It helps standardize data formats and communication protocols across diverse systems, enabling seamless integration between devices from different manufacturers. In M2M communication in IoT, this layer plays a crucial role in eliminating connectivity issues and ensuring reliable data transfer.
The services layer uses protocols such as MQTT and CoAP to ensure interoperability among different IoT devices and networks. It standardizes the way devices interact, which is critical for M2M in IoT, enabling devices to work together efficiently and securely in real-time environments.
Network Services Layer
The network services layer is responsible for connecting IoT devices and ensuring secure, reliable data transmission across various physical and virtual networks. It includes cellular, Wi-Fi, Bluetooth, and satellite communication technologies, all of which are essential for ensuring M2M communication in IoT applications.
This layer also facilitates communication between IoT devices, regardless of their geographical location or the network type used. As IoT networks continue to grow globally, technologies like LPWAN and satellite networks are critical in supporting remote devices in M2M in IoT systems, providing continuous connectivity even in hard-to-reach areas.
To learn more about the different layers in IoT and M2M communication, refer to our blog on the architecture of IoT .
M2M in IoT: Security Challenges
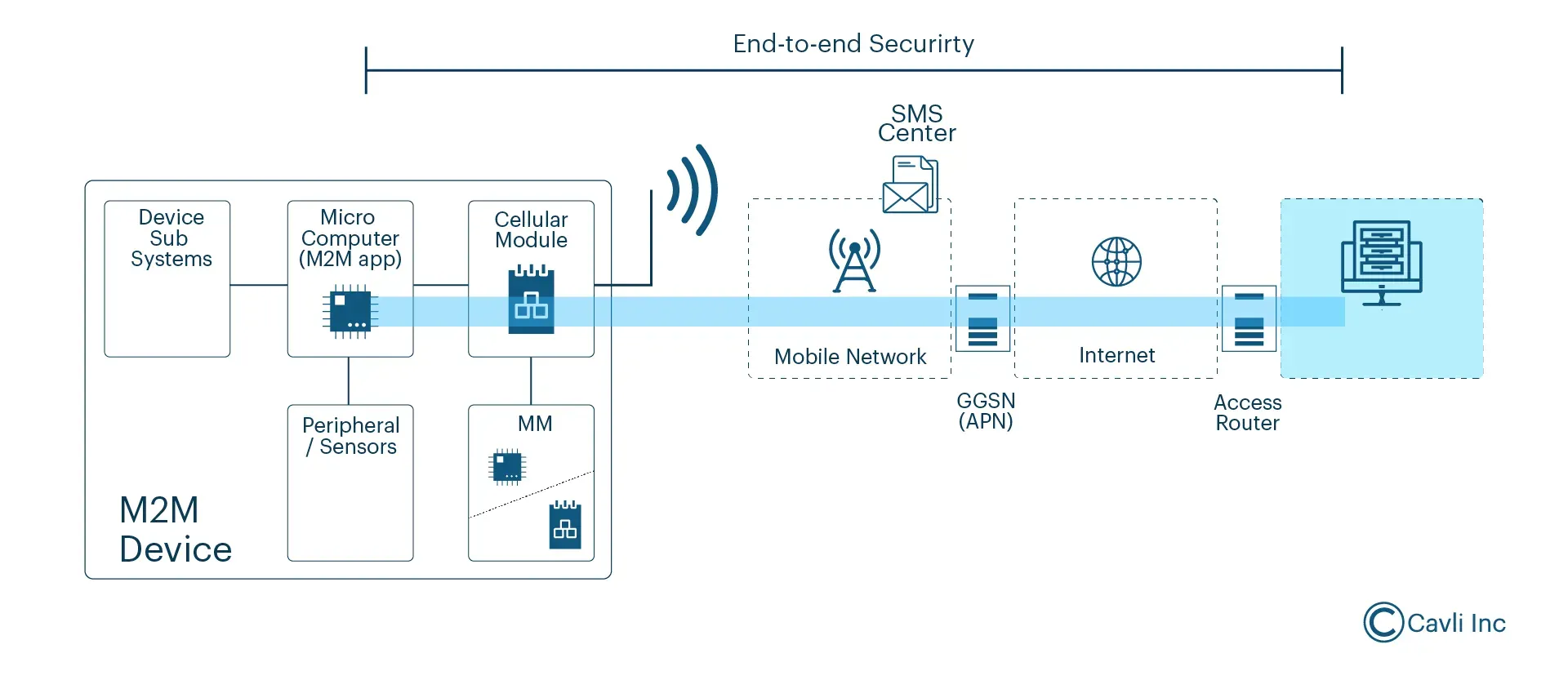
M2M security system
Challenges Associated with M2M and IoT Applications
Data Privacy and Confidentiality
Ensuring the privacy and confidentiality of data in M2M applications is critical. Unauthorized access to critical information can lead to data breaches and misuse.
Authentication and Authorization
Unauthorized devices and users accessing the M2M network is another challenge faced in M2M platforms. Without strong device authentication, illegitimate devices can infiltrate the network and hack inadequate user authorization, leading to inappropriate access levels and allowing unauthorized users to manipulate or access critical information from the M2M systems.
Network Security
As there is an increased number of M2M devices, there are also numerous cyberattacks that affect network security of M2M systems. Interception of data packets, eavesdropping on M2M communications, disrupting the normal functioning of M2M systems with distributed denial of service (DDoS) attacks, altering the information between two M2M devices with Man-in-the-middle attacks, etc., are posing significant cybersecurity risks to the M2M platforms.
Outdated Firmware and Software
Many devices in M2M systems run on outdated firmware and software that are no longer supported or updated by manufacturers. This increases the risk of exploitation, as known vulnerabilities remain unpatched and easily accessible to attackers. Malware targets such M2M devices, infecting the system and allowing attackers to execute unauthorized code.
Security Measures to Improve M2M Security
Data Encryption
Implementing strong encryption protocols, such as AES (Advanced Encryption Standard), ensures that data remains secure during transmission and storage in M2M and IoT applications. Encrypted data is unreadable to unauthorized users, protecting against data breaches and maintaining confidentiality.
Multi-Factor Authentication (MFA)
Using MFA adds an extra layer to M2M security by requiring multiple forms of verification (e.g., passwords, biometric data, and one-time codes). This significantly reduces the risk of unauthorized access in M2M networks, as attackers would need to bypass multiple security barriers.
Network Monitoring and Intrusion Detection Systems
Implementing continuous network monitoring and intrusion detection systems (IDS) helps identify and respond to suspicious activities in M2M platforms in real-time. These systems can detect anomalies, unauthorized access attempts, and potential DDoS attacks, allowing for prompt action to mitigate threats in M2M networks, protecting network integrity.
Regular Software and Firmware Updates
Ensuring that all M2M devices regularly receive software and over-the-air firmware updates addresses security vulnerabilities and patches known exploits. Automated update systems can help maintain up-to-date security measures in M2M solutions, preventing potential threats from exploiting outdated software.
To learn more on over-the-air updates in IoT systems, refer to our blog on FOTA .
M2M in IoT: Real-World Applications
Smart Cities
In smart cities, M2M communication optimizes infrastructure and services. For example, smart traffic lights adjust based on real-time traffic data, waste bins can signal when they need to be removed, and streetlights adjust brightness according to pedestrian and vehicle presence. These M2M systems improve efficiency, reduce costs, and conserve energy in the modern IoT world.
Healthcare
M2M communication enhances remote monitoring and telemedicine in the IoT healthcare sector. Wearable devices and medical implants transmit patient data to healthcare providers in real-time, enabling timely interventions and personalized care.
Industrial Automation
M2M communication facilitates automation and predictive maintenance in industrial settings. Sensors on machinery transmit performance data for analysis, allowing for failure predictions and reduced downtime. Robots in manufacturing plants coordinate tasks and optimize production processes, enhancing efficiency in M2M and IoT applications.
Agriculture
In agriculture, M2M communication enables precision farming by allowing sensors to measure soil moisture, temperature, and nutrients, and communicate with irrigation systems to optimize watering and fertilizer application. The IoT/M2M systems, like drones equipped with sensors, monitor crop health to provide real-time data to farmers for better crop management.
Energy Management
M2M communication supports smart grid applications in the energy sector. Smart meters provide real-time energy consumption data, aiding utilities in managing supply and demand. Distributed energy resources like solar panels and wind turbines communicate with the grid to balance energy production and consumption, integrating renewable sources efficiently in IoT applications.
Closing Notes
M2M communication provides the foundational communication for connected devices to interact, while IoT expands this interaction into a larger ecosystem, enhancing data collection, analysis, and decision-making processes. Machine-to-machine connectivity will drive significant advancements in the IoT environment, leading to smarter, and automated solutions. The future potential of M2M and IoT is immense, offering unprecedented opportunities for innovation, efficiency, and growth. Embracing these technologies will shape the future of our world, unlocking new frontiers of connectivity.
Cavli Wireless IoT Connectivity Modules



